With macOS, you can connect to an FTP server using either a built-in tool or a third-party app. To fully manage your files, and if you want to upload files from your Mac to the remote server, you’ll need to use an FTP client.
To get the best results, we recommend using Commander One, a file manager for Mac with an in-built FTP client.
What is FTP?
FTP, or file transfer protocol, is a cloud storage alternative that allows for uploading and downloading files from a server. Online FTP storage is very secure as access is normally restricted.

✅ Benefits of FTP
Below, we’ve explained some of the most common benefits of using FTP with Mac:
- Great for sharing files
FTP is an excellent way to share files. Its main purpose is to transfer data efficiently between two devices. It’s fast and allows you to move large files with ease. -
Transferring large files
FTP makes it easy to send large files and multiple directories at once. -
Resumable transfers
If your file transfer stops due to connection loss, you can resume it. This eliminates the need to restart from the beginning. -
Easy-to-use
FTP clients come with user-friendly interfaces and let you quickly connect to servers, browse files, and transfer them. -
WordPress website FTP management
You can use FTP to navigate and manage your WordPress site: upload files, and install plugins and themes. -
Cross-platform support
Users across all operating systems (Linux, Windows,macOS) can seamlessly connect to servers.
⛔️ Disadvantages of FTP
FTP has its disadvantages, too, and it’s important to be aware of them. Let’s take a look at some of the main ones:
- Limited encryption
Standard FTP lacks encryption. Consider using protocols like Secure FTP (SFTP) or FTPS (FTP over SSL/TLS), which offer encryption and enable secure file transfers. - Not the most secure option
As convenient as using FTP on Mac is, it’s not a great option for backup or long-term storage. Your login details aren’t encrypted and can be exposed through a “man-in-the-middle” attack. This could lead to your data being stolen while it’s being transferred to or from the server. We explain this in more detail below.
Is FTP safe?
Provided your FTP connection is set up with an ID and a password, it’s fairly safe. But keep in mind that your login details could still be compromised as they’re not encrypted. As mentioned above, FTP servers can be compromised via a “man in the middle” attack. This mostly happens when your data is being transferred.
That’s why many people opt to use SFTP (Secure File Transfer Protocol) or FTPS (FTP over SSL), both of which help make FTP transfers on Mac more safe and secure. Using a third-party FTP client enhances security even further as these apps generally encrypt your data while it is being transferred.
We’ve analyzed the differences between the two protocols in detail. Check out our comparison of FTP and SFTP to learn more about them.
How to connect to FTP on Mac computer via Finder
Using the Finder app to connect to FTP and open the server on Mac is easy and doesn’t take a lot of time. Just follow the guide below to learn how to set up an FTP server on Mac.
Access the Finder menu bar, and then select Go > Connect to Server.
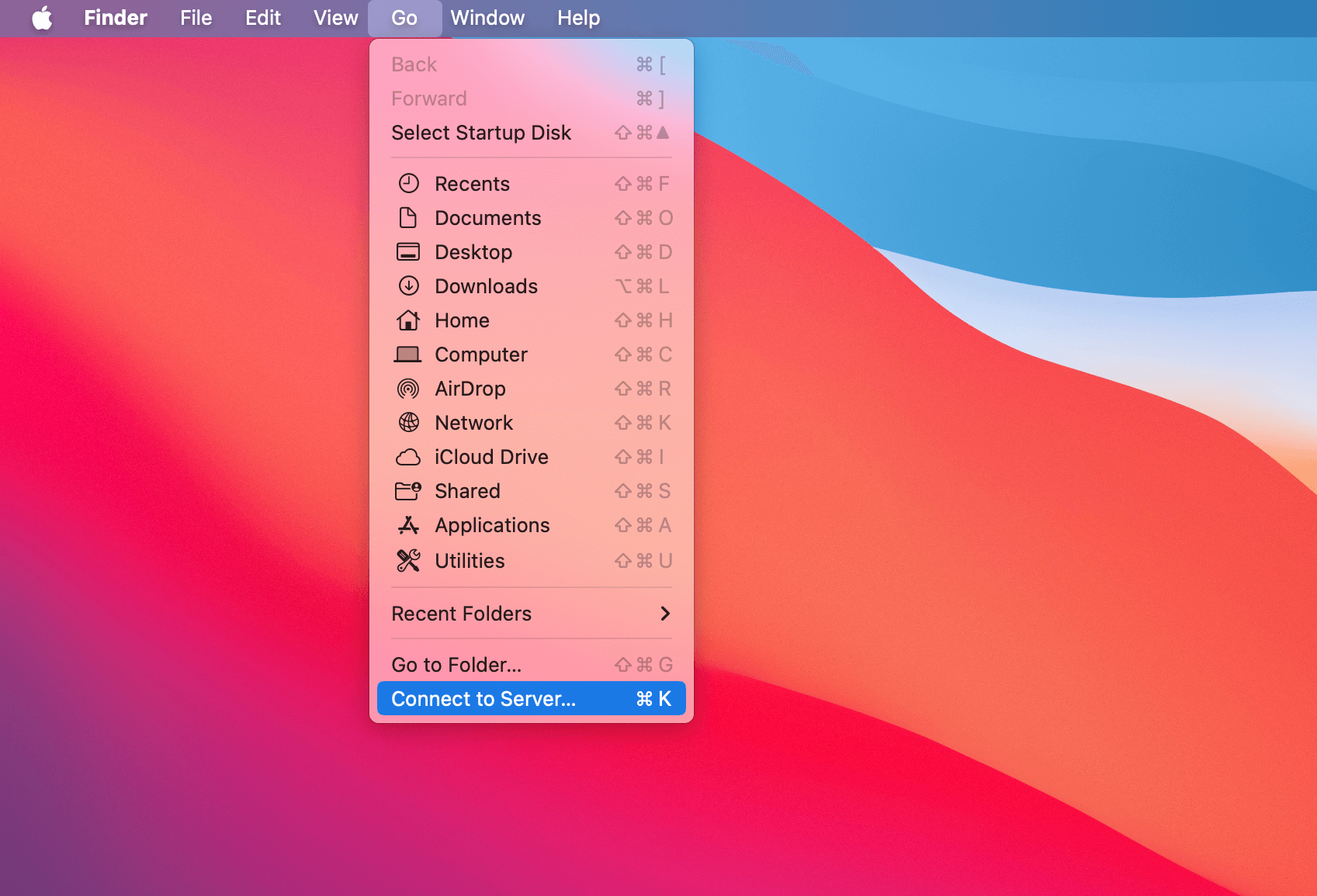
Enter your server’s name or IP address in the server address line.
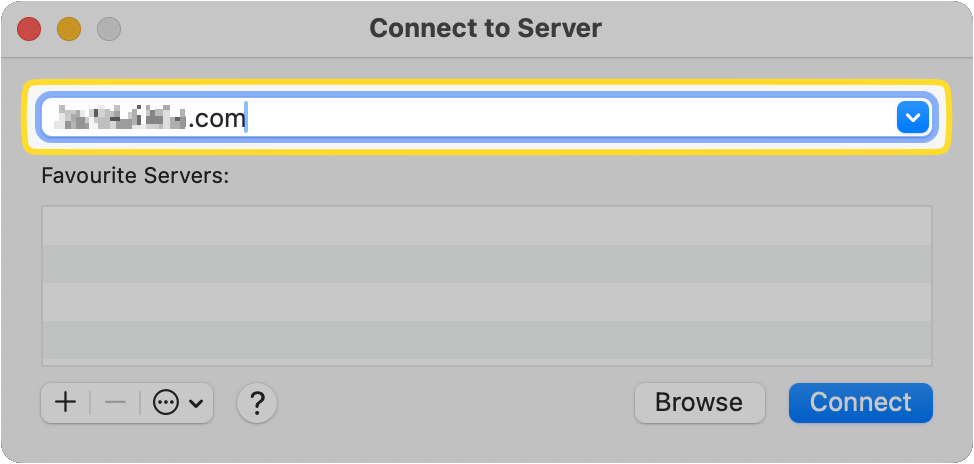
Click the [+] button to add it to Favorite so you can quickly connect FTP to Mac in the future.
![Click the [+] button to add your FTP server to Favorite The [+] button is shown on the Connect to Server pop-up window](https://ftp-mac.com/wp-content/uploads/2024/04/SCR-20240410-snah.png)
Then click on Connect.
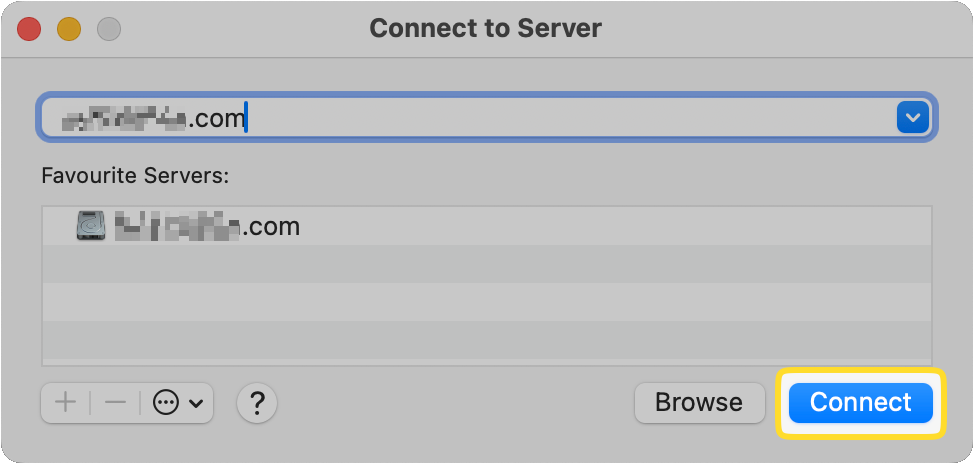
Enter your username and password, then check the box so it’ll be remembered the next time you connect.
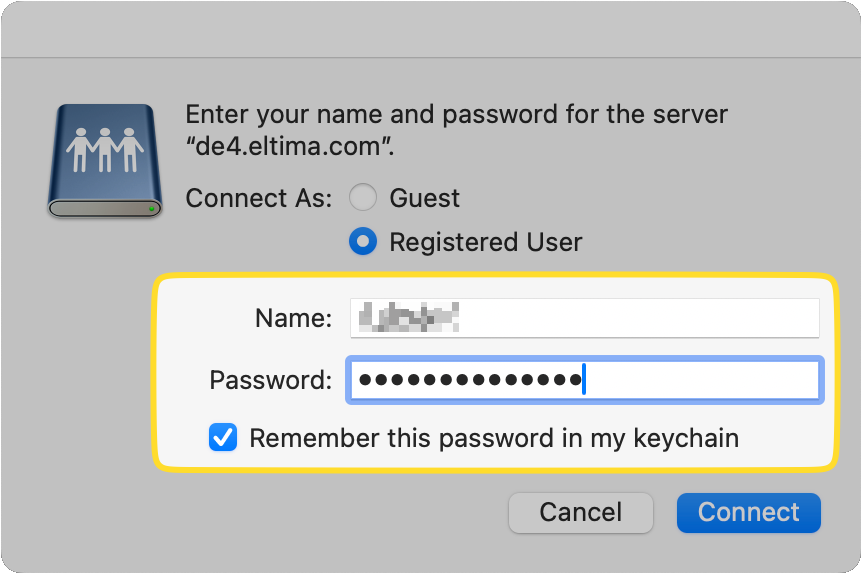
Click on Connect to successfully open FTP in Finder.
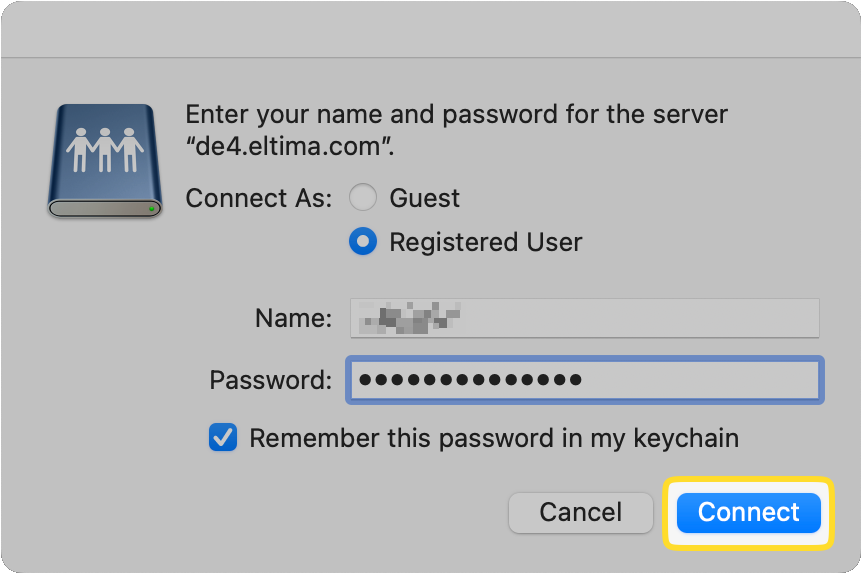
macOS has built-in FTP access for connecting to servers and browsing files. For example, Finder’s “Connect to Server” feature allows you to view and download files from an FTP server, but it offers read-only access. According to Apple, this means you can copy or download files from the server, but you won’t be able to upload files to it. Similarly, FTPS and FTPES are not supported. To upload or edit data, you’ll need a third-party FTP client.
Is it possible to enable FTP on Mac using a browser?
Unfortunately, it’s no longer possible to connect to an FTP server on Mac using a browser. The developers of Google Chrome decided to remove FTP support in their browser. In Mozilla Firefox, it was deprecated in 2020 and can’t be used anymore.
Safari and Opera also don’t support FTP access.
To use FTP from Mac effectively, a dedicated client is your best option.
How to access FTP on Mac through Terminal
Prepare for FTP Server Support in the Terminal to Work
While it is possible to access an FTP on your Mac via Terminal, you first have to install separate utilities since it doesn’t support it natively. It’s a security risk, which is why it’s not already present in the system.
It’s easy to make it work. All you have to do is install Homebrew. In the Terminal window, type “brew install inetutils”. Inetutils is a collection of utilities, which also includes FTP.
It’s also possible to use the Terminal command line to perform basic operations. Just follow our step-by-step instructions to use FTP on Mac through Terminal.
Find the Terminal.app ( / Applications /Utilities).
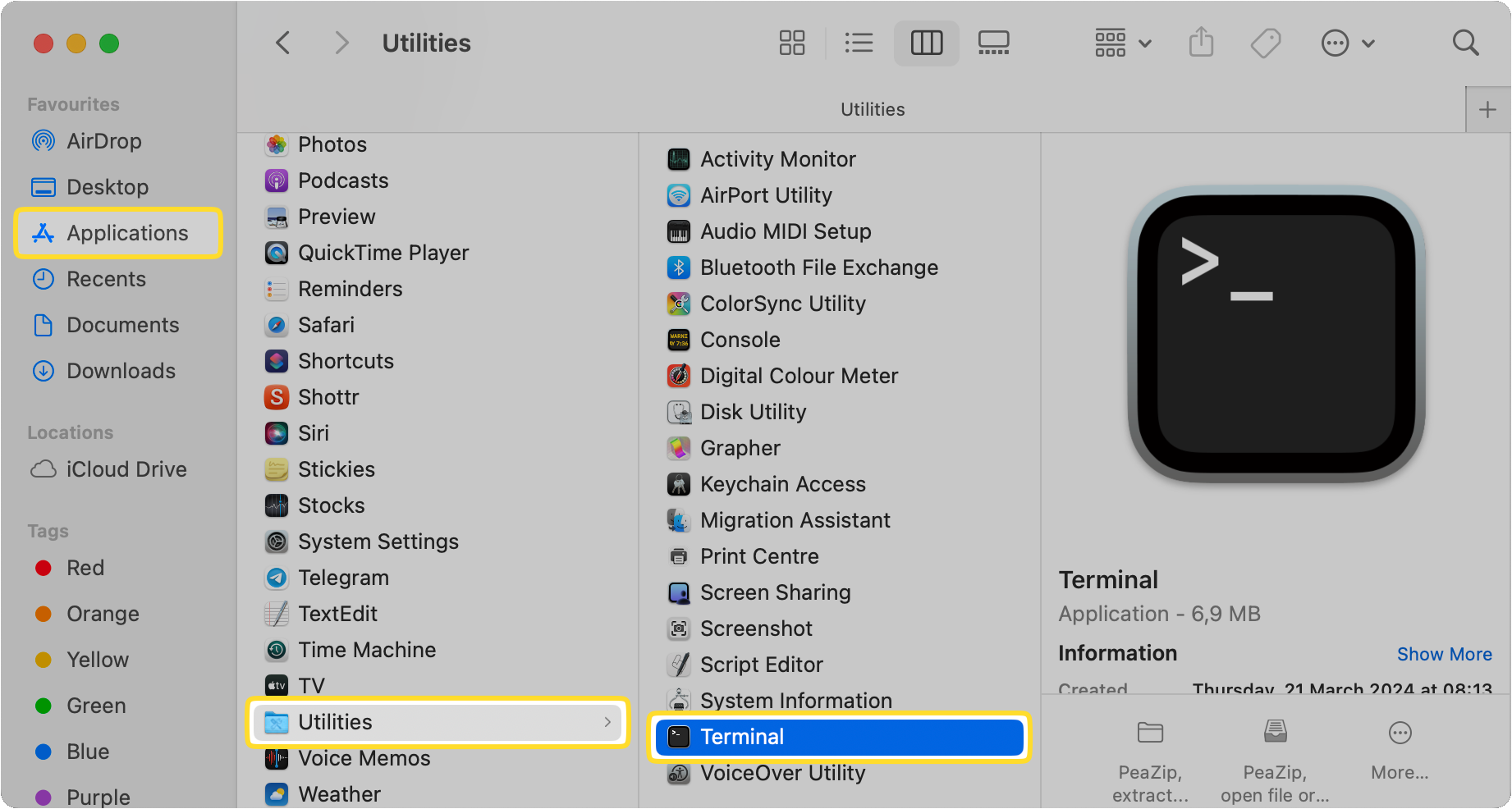
Launch the app.
Type the server address to connect to the FTP server. Ensure you use the following format: ftp ftp.domain.com, and press Enter.
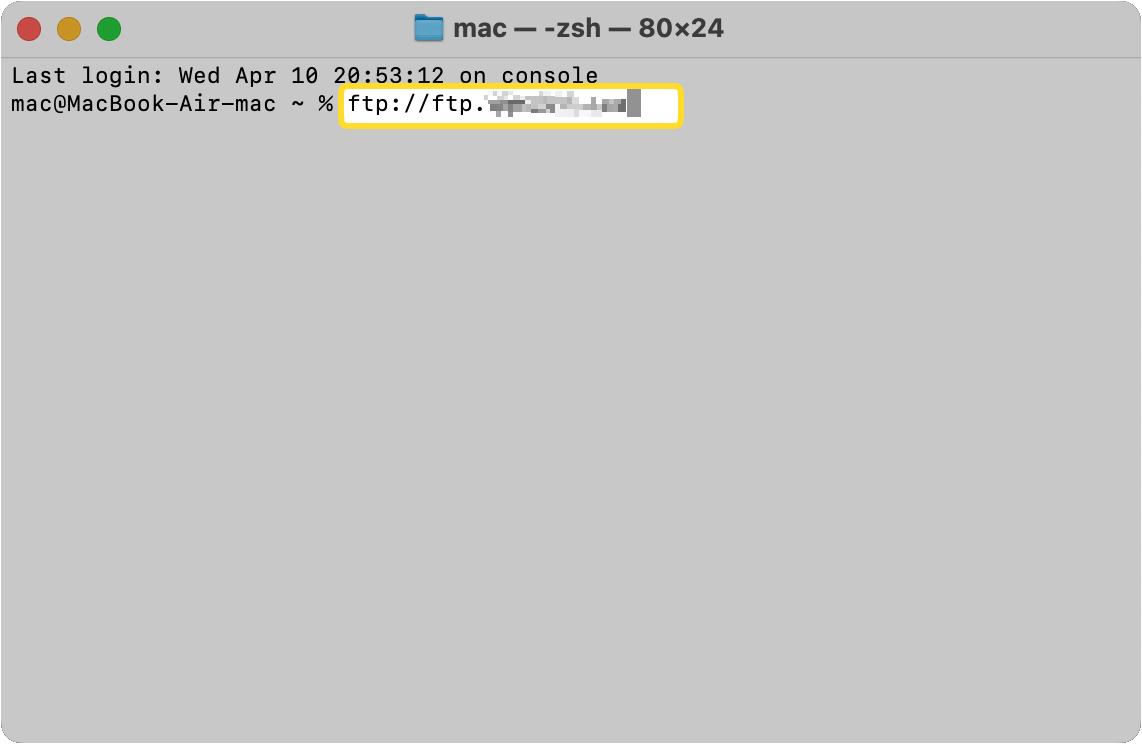
The system will prompt you for your password.
Enter your password.
What criteria to consider when choosing the best FTP client for Mac?
There are several things you should consider when choosing the best FTP client for Mac. Here’s a list of some of them:
The most important thing you should consider is the features and functionalities you want from the app.
Next, consider your budget. Are you willing to pay for a paid app or would you prefer to try out a free one first?
You also need to make sure that the app you want to use is compatible with your current version of macOS.
Finally, read some reviews of the app you want to use to get a good idea of what it’s actually like. If it’s a paid app, we recommend trying out a free trial version first if it’s available.
Alternative third-party FTP Mac clients
Now you know that connecting to an FTP server from Finder only allows you to copy files to and from it. If you use a dedicated client, you’ll be able to do much more, from managing duplicate files to editing files on the server, and comparing versions of server files with locally stored ones.
There are plenty of non-native apps out there to choose from, including dedicated FTP clients and more general file management apps that you can use instead of Finder on your Mac. Here are some of the most popular options:
- Commander One
- Forklift
- CloudMounter
- Transmit
- CyberDuck
Everybody’s needs are different, so make sure the FTP client you choose does what you need it to do. For example, if you’re looking for a Finder alternative, Commander One and Forklift are both great options, offering the ability to sync files between locations and a dual-pane interface. Prefer a basic file transfer tool that supports secure transfer protocols? Try CyberDuck.
Although FTP is an excellent and useful method for transferring files between your Mac and a remote server, you must keep in mind that you always have to use either SFTP or FTPS. This is to ensure that your files are kept safe while they’re being transferred.
It’s completely up to you whether you simply connect to an FTP server from Finder, or use a third-party software for file transfer and management. Using a dedicated app gives you more functionality and control, and may make it easier to batch download/upload files, too.
Commander One – the best FTP for Mac software option
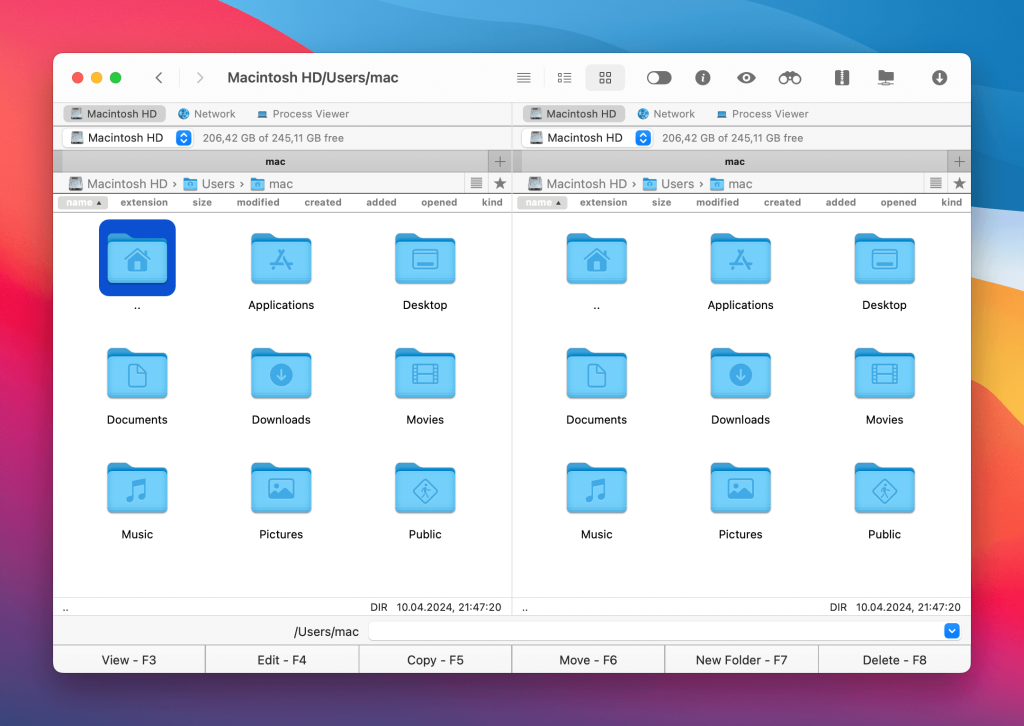
If you’re considering a third-party app to mount FTP on Mac, why not try Commander One? This FTP/SFTP/FTPS client for Mac makes it quick and easy to access an FTP server on Mac in just a couple of clicks. Not only can you access files, you can name, copy, delete, move, or edit them, just as though they were stored locally on your computer.
Commander One is intuitive and easy to use, yet packs in loads of advanced features such as work with archives, iOS devices, MTP devices, process viewer, encryption on online connections, and more. The dual-pane interface makes it easy to see and manage all your files and folders at any time.
Pros
- Built-in FTP/SFTP/FTPS client
- Supports cloud computing services
- Support for hotkeys
- Multiple tabs support
- Terminal emulator
- Encrypts transfers and connections
Cons
- Can’t synchronize directories
- There’s no multi-rename feature
Conclusion
There are several ways to connect to an FTP server on Mac. Some methods are more user-friendly and secure, while others may be less suitable for beginners.
For example, macOS Finder only supports downloading files from the server, not uploading them. For additional functionality, you can use Terminal. However, if FTP isn’t working on your Mac or you’re having trouble connecting to the server, a dedicated application like Commander One is highly recommended.
Frequently Asked Questions
You can enjoy a wider range of functionality and more secure connection by using a third-party FTP client or app. Most apps allow you to view, copy, rename, edit, and move files as though they were stored locally on your computer. The majority of third-party clients also offer encryption to keep your data safe as it is being transferred. You could simply use Finder on your MacBook, but then you won’t enjoy the same range of functionality.
Although it is possible to access an FTP server on Mac using built-in solutions such as Mac Terminal commands or Finder, you won’t be able to upload files. If you want to upload to an FTP site from your MacBook, the best option is to use a third-party app like Commander One.