The need for storing important information has always existed. Ever since computers were created and basic networks started appearing, people have wanted to get easy access to all their data. In the ongoing debate between FTP vs SFTP, the two most popular protocols for transferring files, it’s all about finding the best way to keep our data safe and accessible.
They may sound alike, but they have many characteristics that make them unique. Although created a long time ago, they still remain widely popular even today.
What is FTP and SFTP?
Below, we’re going to explain how FTP and SFTP differ from each other. You’ll also learn what these abbreviations mean and how they work.
FTP Meaning
FTP is a popular file transfer method that is now being used everywhere and hasn’t gone through many changes since its invention in 1971.
At the time of its creation, it was not generally assumed that activities on the Internet would actively be targeted by hackers, so FTP was not created with features to deal with the sort of cybersecurity threats we see in the news today.
How does FTP work
The File Transfer Protocol, or more popularly known as FTP, is designed to organize the exchange of data between your PC and a remote server. This process is similar to when you copy a file in one folder and transfer it to another. Using FTP, you get access to the disk space that is allocated to you by the host.
FTP exchanges data using two separate channels, known as the command channel and the data transfer channel. Keep in mind that they’re both unencrypted, so any data sent through them could be intercepted.
Available functions in FTP
There are tons of features that are provided by FTP. Here are some of them:
- Download files from the remote server.
- Upload sites to the hosting platforms.
- Transferring files to different types of FTP servers.
There are special programs available for PC and Mac that allow you to use FTP. These are called “FTP clients.” Their functions are generally the same and they mostly differ in how they look and their ease of use. These dedicated applications can be installed on any computer with any OS, be it Windows, Unix, or macOS.
You can see how an FTP server makes for a good replacement for portable storage media. One of its biggest advantages is that you can easily transfer your data to another computer. All you have to do is move it to the FTP server and then just download it from another computer. This method is more convenient and beneficial for Network users.
Pros
- Allows you to transfer many files and directories
- High transfer speeds
- No limitations when it comes to file size (only applies to single files)
- Ability to add items to a queue
- Supported by a lot of hosts
Cons
- Bad security due to usernames and passwords being stored in text form
- Servers can be spoofed to send data to a random unknown port on any unauthorized computer
- No support for encryption
- It’s easy to wipe out all of the files (especially for new users)
Additional info: How to use FTP on Mac
SFTP Meaning
SFTP stands for Secure File Transfer Protocol. It’s a completely different technology that’s based on the SSH File Transfer Protocol (Secure Shell) and has nothing to do with FTP. When it comes to SFTP vs FTP, the former is generally more secure since it has a built-in encryption system. Despite this, SFTP has not been adopted as the official standard of the Network yet.
How does SFTP work
The application layer protocol SFTP was developed as an extension to SSH-2. It is used to copy and execute operations with files on top of a secure connection. In most cases, it uses port 22. SFTP assumes that it is running over the established secure channel, that the server has already authenticated the client and that the client ID is available to the protocol.
SFTP provides two ways to authenticate connections. Like FTP, you can simply use the user ID and password. However, with SFTP client, these credentials are encrypted, which gives it a great security advantage over FTP.
Another authentication method that you can use with SFTP is SSH keys. This assumes, first of all, the generation of the private key SSH and the public key. Then, you send your public key SSH to your trading partner, and they upload it to their server and after that connect to your account. When connecting to your SFTP server, their client software will transfer their public key to the server for authentication. If the public key matches your private key, along with any user or transmitted password, the verification will be passed. The user authentication ID can be used with any combination of a key and/or password authentication.
Features and functions of the SFTP protocol
Just like FTP, SFTP also has a plethora of features and functions. We’ve listed some of them below:
- Allows you to resume certain functions, interrupt a transfer and delete the file.
- Used as a subsystem of version 2 of SSH.
- Downloaded files can be combined by their main attributes (such as timestamps) – a great advantage over FTP, which doesn’t have downloading conditions.
Pros
- The connection is always secure due to the encryption feature that comes with it
- Login information is stored securely and isn’t easy to access
- Ability to use SSH keys, making logging in even more secure
- Does not require root access for installing software
Cons
- SSH Keys are hard to use and require prior knowledge
- Does not stop the transfer of information to third-parties which can lead to breaches and data leaks
- Users have to store SSH keys on their computer which can lead to theft or impersonation
Additional info: How to set up Mac as an SFTP server
What is SSH?
SSH is a network protocol that lets you access a remote computer securely over an unsecure network. Since it’s always encrypted, any information you send through it is protected and can’t be accessed without authorization.
Mainly used for file transfers, running commands on a remote computer, and remote system administration, SSH is one of the most popular protocols in use today.
SSH uses public-key cryptography to allow the host and authorizes them to access the information stored on the server. There are many ways to use SSH, one is to automatically assign two pairs of public and private keys to encrypt the network before the file transferring process occurs, thus generating a password that will allow the user to connect to the server.
Commander One is a perfect FTP/SFTP client for Mac
Commander One is a powerful dual-pane file manager for macOS that makes file handling fast and efficient. Along with managing local files, it offers built-in FTP/SFTP support, letting you easily connect to remote servers.
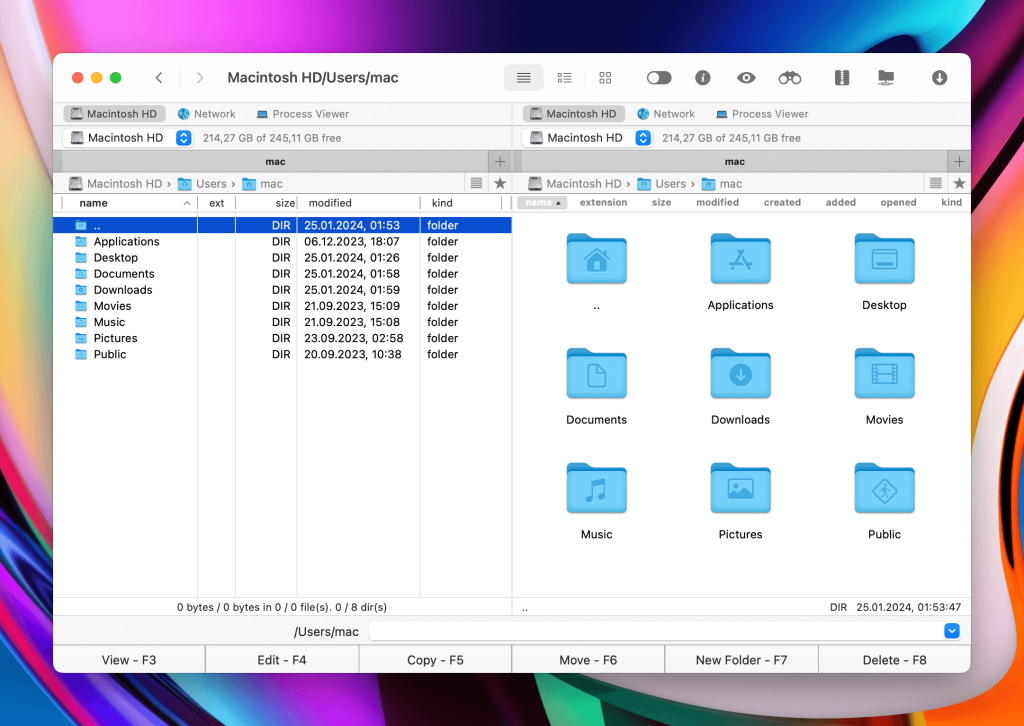
Commander One is a great combination of all the features you would need for a fast and secure data transfer. With its minimalistic dual-panel interface, you would be able to work with all your files and folders easily. Moving them around without having to open additional tabs is an effortless process.
Moreover, the app’s PRO pack allows you to seamlessly mount all the popular cloud storages like Dropbox, Amazon S3, Google Drive, and OneDrive on your Mac. You can also manage and access all the information that’s stored in those services as if they were on your local hard disk.
Besides that, you can easily connect your Android smartphone, and other devices that support MTP connections, and manage all the data stored in there without any effort. You can try Commander One out for free and see how it works.
Difference between FTP and SFTP
To help you understand the differences, we’ve added a comparison table below that highlights some of the main features of the two data transfer methods. Here’s our handy FTP to SFTP comparison:
| Parameter | FTP | SFTP |
| Creation Date | 1971 | 1997 |
| Complete Name | File Transfer Protocol | Secure FTP Protocol |
| Login Methods | User ID & Password | User ID & Password SSH Keys |
| Encryption | Comes with no encryption | Always encrypts information before it’s sent to the server |
| Architecture | Client-server | SSH |
| Protocol | FTP is TCP/IP protocol | SSH Protocol – Remote Application Login |
| Number of channels used | 2 | 1 |
| Widely Adapted | Yes | No |
| Method of Transfer | Direct transfer | Tunneling |
| Inbound Port | Port 21 | Port 22 |
| Outbound Port | Port 21 | Port 22 |
Encryption Methods for FTP and SFTP
While FTP does not come with built-in encryption, there are numerous file transfer protocols similar to it such as FTPS and SFTP that offer this kind of privilege. SFTP will encrypt everything that is being transferred onto the server through a special algorithm through one connection output. It’s worth knowing this protocol doesn’t only apply to files, but to the login information as well. Your ID and password are carefully encrypted and stored, thus minimizing the risk of potential data breaches.
The basis of SFTP is a secure shell, an SSH encryption method for file transfer.
SFTP runs on TCP port number 22, but with a bit of tweaking, users can assign any port they want. The SSH-2 version is built into SFTP, which provides an extra layer of full encryption when connecting to the server.
Which should you choose
So should you use FTP or SFTP? There are plenty of things to take into account. Do you want something that is supported by the majority of the server at the cost of privacy and security or would you like something that encrypts your information and makes it harder for it to fall in the wrong hands?
We strongly recommend that you look at the pros and cons of each protocol and then decide which one suits your needs the best. Most people prefer to use FTP because of its accessibility and ease of use, but if you regularly deal with sensitive information, then you might want to use SFTP, even though the SSH keys may be hard to understand at first.
All in all, both technologies are quite reliable when it comes to transferring files at high speeds and will very likely continue to be used in the future.